Introduction to Cybersecurity in Video Technology

Table of Contents
The intertwining of cybersecurity and video technology has become a focal point for both tech professionals and everyday users. With digital video systems deeply embedded in various sectors, from personal security to global enterprises, understanding and mitigating the associated cyber risks is paramount. This comprehensive exploration of cybersecurity in video technology will shed light on current challenges, strategies for protection, and future advancements.
The Growing Significance of Cybersecurity in Today’s Digital Era
The digital age has transformed data into a critical asset, necessitating robust protection measures. Cybersecurity transcends its traditional IT confines, becoming a vital component in safeguarding digital data. In the context of video technology, which permeates various aspects of our lives, from surveillance to communication, the imperative for stringent cybersecurity measures has never been more pronounced.
Overview of Video Technology and Its Vulnerabilities
Video technology, having shifted from rudimentary analog systems to advanced digital formats, is now more susceptible to cyber threats. These threats range from basic unauthorized access to sophisticated hacking attempts. Understanding these vulnerabilities is the first step in creating a resilient defense against potential cyber intrusions.
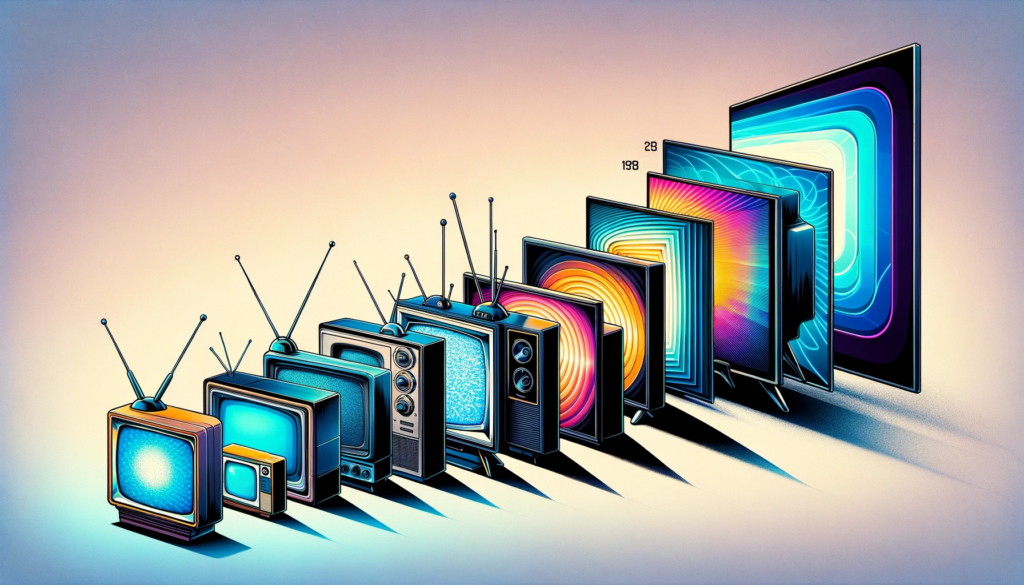
The Evolution of Video Technology
The transformation of video technology over the years has been both revolutionary and instrumental in shaping current digital media practices.
From Analog to Digital: A Brief History
The transition from analog to digital video technology marked a significant milestone. This shift not only enhanced the quality and accessibility of video content but also introduced new vulnerabilities. Digital platforms are inherently more susceptible to cyber attacks, making their security a crucial concern.
The Integration of AI and IoT in Modern Video Tech
The incorporation of Artificial Intelligence (AI) and the Internet of Things (IoT) into modern video technology has enhanced capabilities but also compounded cybersecurity challenges. AI-driven surveillance systems and IoT-enabled devices necessitate a new paradigm in cybersecurity measures to protect against sophisticated threats.
Understanding Cyber Threats in Video Tech
The realm of video technology is not immune to the ever-evolving landscape of cyber threats, necessitating a vigilant and informed approach to security.
Common Cybersecurity Risks in Video Technology
The cybersecurity risks in video technology are varied, encompassing unauthorized access, data interception, and advanced persistent threats. A deep understanding of these risks is imperative for the development of robust countermeasures to safeguard video systems.
Case Studies: Real-world Cyber Attacks on Video Systems
Analyzing real-world cyber attacks on video systems reveals the tactics employed by cyber criminals. These case studies provide crucial insights into the vulnerabilities exploited and the strategies for defense.
Protective Measures and Best Practices
A proactive stance on cybersecurity is vital for the protection of video technology systems against emerging threats.
Strategies for Securing Video Data
Effective strategies for securing video data encompass a range of measures, from frequent software updates and strong encryption methods to secure network configurations. These strategies form the backbone of defense against unauthorized access and data breaches.
Implementing Robust Encryption and Access Controls
Utilizing advanced encryption standards and implementing stringent access controls is essential for safeguarding video data. These measures ensure that only authorized individuals have access to sensitive video content, thereby significantly reducing the risk of security breaches.

The Role of AI in Enhancing Video Security
AI is revolutionizing the field of video security, providing cutting-edge solutions for real-time threat detection and response.
AI-driven Surveillance and Threat Detection
AI-driven surveillance systems can autonomously detect unusual activities or potential security breaches, enabling a more efficient and effective response to security incidents. This technology represents a significant advancement in the proactive monitoring and safeguarding of video systems.
Balancing AI Efficiency with Privacy Concerns
While AI significantly boosts video security, it also raises privacy concerns. Balancing the efficiency of AI technologies with privacy considerations is a critical aspect of their ethical application in video surveillance systems.

Regulatory Compliance and Industry Standards
In the world of video technology security, adhering to regulatory compliance and industry standards is non-negotiable.
Understanding GDPR, HIPAA, and Other Regulations
Familiarity with data protection and privacy regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) is essential. Compliance with these regulations is key to maintaining the confidentiality and integrity of video data.
Adhering to Industry Standards for Video Security
Following industry standards such as the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) standards helps in establishing a comprehensive cybersecurity framework. This adherence ensures that video systems are protected according to globally recognized best practices.

Cybersecurity Training and Awareness
Fostering a culture of cybersecurity awareness is as crucial as implementing technical safeguards.
Importance of Employee Training in Cybersecurity
Regular training sessions for employees are pivotal in equipping them with the necessary skills to identify and mitigate cyber threats. These training programs are an essential component of a comprehensive cybersecurity strategy.
Developing a Culture of Security Awareness
Building a culture where every individual within an organization is cognizant of and committed to cybersecurity best practices is vital. This cultural shift ensures that all stakeholders contribute to the security of video technology.
Future Trends in Video Technology Security
Staying abreast of future trends in cybersecurity is crucial in the fast-evolving landscape of video technology.
The Role of Quantum Computing in Cybersecurity
Quantum computing is poised to revolutionize cybersecurity with its potential to create virtually unbreakable encryption. This advancement could significantly enhance the security of video technology systems.
Predictions for Future Cyber Threats in Video Tech
Anticipating future cyber threats allows for the development of preemptive security measures. Understanding these evolving threats is key to maintaining the security and integrity of video technology systems.

Case Study: Implementing Cybersecurity
Examining real-world examples of cybersecurity implementation offers valuable lessons and best practices.
Successful Cybersecurity Implementation in a Major Corporation
A case study of a major corporation’s successful cybersecurity implementation provides a practical blueprint for others. This example highlights the strategies employed and the challenges overcome in securing video technology.
Lessons Learned and Best Practices
Learning from the successes and shortcomings of others in the field of video technology security is invaluable. These lessons inform the continuous refinement of cybersecurity strategies and best practices.

Challenges and Limitations in Cybersecurity
Acknowledging and addressing the challenges and limitations in cybersecurity is essential for the ongoing improvement of security measures.
Addressing the Complexity of Video Tech Security
The complexity of modern video technology demands equally sophisticated and adaptable cybersecurity solutions. Addressing these complexities is key to developing effective and resilient security measures.
Balancing Usability with Security
Striking a balance between user-friendliness and robust security is crucial. Security protocols must be both effective and manageable to ensure widespread adoption and adherence.
User Responsibility in Video Security
End-users play a pivotal role in maintaining the security of video technology systems.
Role of End-users in Maintaining Video Security
Educating end-users on security best practices and the importance of adhering to security protocols is critical. This education ensures that users are well-equipped to contribute to the overall security of video technology systems.
Best Practices for Users to Enhance Security
Providing users with clear guidelines and best practices for video security is essential. These guidelines help users understand their role in maintaining the security of video technology and the best practices to follow.

Innovations in Video Tech Cybersecurity
Innovations in cybersecurity are crucial for staying ahead of cyber threats in video technology.
Emerging Technologies and Their Impact on Cybersecurity
Emerging technologies such as blockchain are providing new ways to secure video data. These technologies offer decentralized and tamper-proof methods for protecting video content.
How Blockchain and Other Innovations Are Shaping the Future
Blockchain and other emerging technologies are reshaping the cybersecurity landscape. These innovations offer novel approaches to securing video data and protecting against cyber threats.

Cybersecurity and Ethical Considerations
Ethical considerations are paramount in the application of cybersecurity measures in video technology.
Navigating the Ethical Landscape of Video Surveillance
Balancing the benefits of video surveillance with ethical and privacy concerns is essential. Navigating this landscape requires a careful and responsible approach to data collection, storage, and usage.
Protecting Privacy in an Age of Increased Surveillance
In an era of pervasive video surveillance, ensuring privacy is a significant challenge. Protecting privacy requires a nuanced approach to the collection and handling of video data.
Securing Video Content in the Cloud
The cloud has become a preferred storage solution for video content, but it introduces its own set of cybersecurity challenges.
Cloud-based Video Storage: Risks and Rewards
Understanding the risks and rewards associated with cloud-based video storage is crucial. This understanding helps in making informed decisions about the security of video data stored in the cloud.
Best Practices for Securing Video in the Cloud
Implementing best practices for cloud security is essential for protecting video content against cyber threats. These practices ensure the integrity and confidentiality of video data stored in cloud environments.

Collaboration and Partnerships in Cybersecurity
Collaboration and partnerships play a crucial role in developing comprehensive and effective cybersecurity solutions.
The Importance of Collaboration Among Tech Companies
Collaboration between technology companies and cybersecurity experts leads to the sharing of knowledge, resources, and best practices. This collaboration enhances the overall effectiveness of cybersecurity measures in protecting video technology.
Case Examples of Successful Security Partnerships
Examining successful security partnerships provides insights into the collaborative efforts that have led to significant advancements in video technology security. These case examples highlight the benefits and outcomes of such partnerships.

Conclusion: The Future of Cybersecurity in Video
The field of cybersecurity in video technology is dynamic and ever-evolving. As technology advances, so do the cyber threats and the measures to counter them. The future of video technology security lies in innovative solutions, informed user practices, and collaborative efforts to ensure the safety and integrity of video content.
FAQs
What are the most common cybersecurity threats in video technology?
The most common cybersecurity threats in video technology include unauthorized access, data breaches, malware attacks, and interception of video feeds. These threats can originate from various sources such as hackers, disgruntled employees, or even competitors. The vulnerabilities in video technology, such as weak passwords, unsecured network connections, and outdated software, often exacerbate these threats.
How does AI enhance cybersecurity in video technology?
Artificial Intelligence (AI) enhances cybersecurity in video technology by enabling advanced threat detection and response capabilities. AI algorithms can analyze video data in real-time to identify abnormal patterns or suspicious activities, offering quicker and more accurate threat detection compared to traditional methods. Additionally, AI can help automate routine security tasks, such as monitoring video feeds or updating security protocols, thus reducing the likelihood of human error.
What are some best practices for securing video content?
Best practices for securing video content include using strong encryption standards for both stored and transmitted video data, implementing robust access controls, regularly updating software and firmware to patch vulnerabilities, and using secure network connections. Additionally, conducting regular security audits and employee training programs to raise awareness about potential threats and best practices in cybersecurity are also crucial.
How do regulations like GDPR impact video technology security?
Regulations like the General Data Protection Regulation (GDPR) impact video technology security by setting strict standards for data protection and privacy. Companies must ensure that their video technology systems comply with these regulations, which include obtaining consent for collecting video data, ensuring the data is stored securely, and providing individuals with the right to access or delete their data. Non-compliance can lead to significant penalties and damage to the company’s reputation.
What role do end-users play in maintaining video security?
End-users play a critical role in maintaining video security. They are often the first line of defense against security breaches. End-users can contribute to video security by practicing good cybersecurity hygiene, such as using strong, unique passwords, being cautious of phishing attempts, and ensuring their devices and applications are up-to-date with the latest security patches. They should also be aware of the company’s security policies and report any suspicious activities.
What are the emerging technologies in video tech cybersecurity?
Emerging technologies in video tech cybersecurity include blockchain for secure and tamper-proof data storage, quantum computing for advanced encryption, and AI and machine learning for improved threat detection and response. Additionally, the use of biometric authentication methods, such as facial recognition or fingerprint scanning, is becoming more prevalent for enhancing access control in video technology systems. These technologies are continually evolving to offer more sophisticated means of protecting video data against cyber threats.
4 Useful References to Articles on Cybersecurity in Video Technology
- IDIS Video Cybersecurity (International Security Journal):
- https://internationalsecurityjournal.com/idis-video-cybersecurity/
- This article likely cybersecurity solutions and practices by IDIS, focusing on how they secure video surveillance data against cyber threats, with an emphasis on encryption and access control measures.
- MDPI Article on Cybersecurity in Video Technology:
- https://www.mdpi.com/1424-8220/23/8/4117
- A scientific publication in the journal Sensors by MDPI, discussing cybersecurity within the context of video technology. The article may present new research findings, technical security solutions, or a review of current practices in safeguarding video communications and storage.
- SAGE Journals – Research on Video Technology and Cybersecurity:
- https://journals.sagepub.com/doi/10.1177/1046878120933312
- This link leads to a scholarly article that might explore the use of video technology in cybersecurity training, awareness, or education, highlighting innovative approaches like simulations or interactive learning modules.
- University of Melbourne – Cyber Security Excellence & Video Enhanced Storytelling:
- https://cis.unimelb.edu.au/cyber-security-excellence/video-enhanced-storytelling
- Hosted by the University of Melbourne, this content likely discusses how video storytelling can be leveraged to enhance cybersecurity education and awareness, potentially featuring case studies or projects that illustrate key concepts in an engaging manner.
The above links and contexts offer a diverse view into how video technology intersects with cybersecurity, from technical defenses against hacking to innovative educational strategies.
These resources offer a comprehensive view of the different aspects of cybersecurity in the realm of video technology, from securing video conferencing tools to protecting video content and streaming services.
Remember, the field of cybersecurity is rapidly evolving, so it’s important to check these sources for the most current information and articles.
Cybersecurity in Video Technology an article by Nicole Delgado 2024 | CMO | Explainer Video Company | Animated Explainer Videos For Business